Cyber Security Courses
Sign up today with our early bird offer and get 20% off
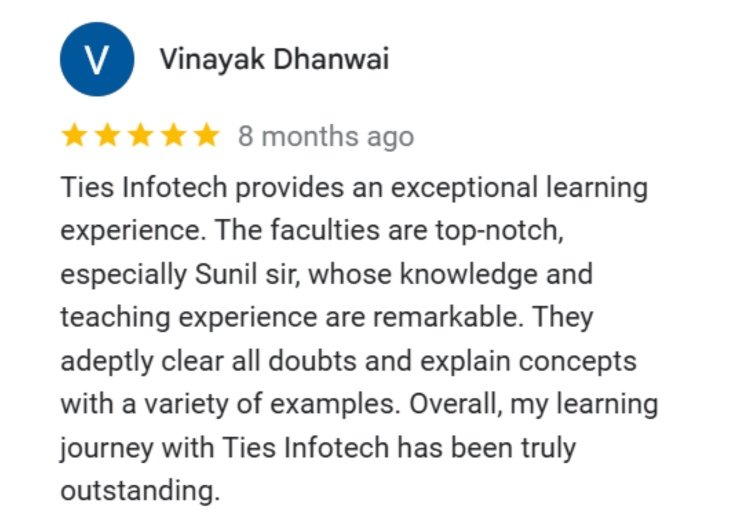
Proud of our Alumni
Our Accomplished Graduates


List goes on...
Why Choose Ties Institute
Our Benefits




What will You Learn
Course Modules
- Module 1
- Module 2
- Module 3
- Module 4
Module 1 – Introduction to Cybersecurity
-
Introduction to Cybersecurity
- What is Cybersecurity
- Understanding the Cybersecurity Terminology
- CIA Triad, Separation of Duties, Org Structure
- Top Down and Bottom-up Approach
-
Fundamentals of Networking
- Introduction to Networking
- Understanding Networks and Networking
- Types of Networks: LAN, MAN, WAN, and Internet
- Network Topologies: Bus, Ring, Star, and Mesh
- Essential Network Components: NIC Cards, MAC Addresses, Media, and Devices (Hubs, Switches, Routers, Firewalls)
- OSI Reference Model and TCP/IP Model
- Understanding IP Addresses
- Types of IP Addressing: IPv4 and IPv6
- Subnetting Techniques
-
Operating Systems Basics
- Linux Basics
- Windows Basics
Module 2 – Advanced Cybersecurity Concepts
- Information Gathering
- Proxy & VPN
-
Risk Management Fundamentals
- Asset Management, Threat and Vulnerability
- Threat, Threat Agent, Exploit, Quantitative and Qualitative Risk Assessment
- Risk Management Lifecycle (Assessment, Analysis, Mitigation, and Response)
- Risk Management Framework (ISO31000, ISO27000, Steps involved in Risk Management Framework)
-
Scanning
- What is Scanning
- What is Enumeration
- Scanning Methodology
- Blue Teaming, Red Teaming, Purple Teaming
- Vulnerability Assessment
- Penetration Testing
-
Phishing
- What is Phishing
- Phishing Techniques
- Spear Phishing
- Whaling
- Piggybacking
- Watering Hole
-
Mobile Security
- Device Encryption
- Internal Locks (Voice, Face Recognition, Pattern, PIN, Password)
- Application Installation Control, Asset Tracking (IMEI)
- Mobile Device Management, Removable Storage (SD Card, Micro SD, etc.)
- Gaining Access to Mobile
Module 3 – Advanced Cybersecurity Techniques
-
Introduction to Metasploit
- Understanding Local Exploit & Remote Exploit
- Understanding Exploits, Payloads, Auxiliary, etc.
- Gaining Access to Endpoints Using Metasploit
-
Malware
- What is Malware
- Types of Malware
- Privilege Escalation
- Unauthorized Application Execution
- Virus, Worms, Logic Bomb, Trojan, Backdoor, Sniffing, Zero-Day Attack, Ransomware, Rootkit, Spyware, etc.
-
Cryptography
- What is Cryptography
- Types of Cryptography
- Digital Signature, Hashing
- Cryptography Algorithms (DES, AES, IDEA, Twofish)
-
Denial of Service Attack & Defenses (DoS & DDoS)
- What is DoS
- What is DDoS
- Botnets
- DoS/DDoS Attack Techniques
-
Wireless Hacking
- What is a Wireless Network
- Types of Wireless Networks
- Different WiFi Standards
- WiFi Attacks
-
Network Security
- OSI Model, Attacks in OSI Layers, Network Types, Network Methods and Standards, Hardware Devices
- VPN Protocols, Firewall and Perimeter Security
- Firewall, Types of Firewalls, DMZ, Honeypot
- Different Types of Network Attacks
Module 4 – Advanced Security Practices
-
Firewalls
- What is a Firewall
- Different Firewall Technologies
- Packet Filtering Firewall
- Stateful Firewall (Designing Security with Firewall, NAT, Security Policy, Content Management, User Identity Management, Logging, Reporting)
-
IoT and Internet Security
- Network Segmentation (Isolation), Logical Isolation (VLAN), Physical Isolation (Network Segments)
- Application Firewalls
- Firmware Updates
-
Vulnerability Assessment and Pen Test
- Steps Involved
- Test Types
- Test Strategies
- Reporting
-
SOC (Security Operations Center)
- Introduction to SOC(S)
- Roles under SOC
Get 20% OFF
- 00Days
- 00Hours
- 00Minutes
- 00Seconds
Know about Your Trainer
Trainer's Profile
Mr. Sunil Singh sir
Senior Technical Trainer with over 16+ years experience in IT.
Proficient in Cisco and Redhat, Cyber Security and Ethical hacking, Forensic Investigation, Microsoft, and AWS Platforms… CCNA, RHCE, MCSA, AWS, CEH, CHFI Certified Trainer.
What you'll do in our course
Co-Curricular Extra Activities
Choose the Best
Why Ties Certified Security Associate Courses?
- Practical Learning: We emphasize practical learning through real-world simulations.
- Expert Trainers: Our trainer brings over 16 years of professional experience.
- Comprehensive Curriculum: Learn from a well-rounded syllabus that covers the latest trends and techniques in cybersecurity.
- Stepping Stone to Advanced Certifications: Build a solid foundation for globally respected certifications like OSCC & OSCP.
- High Demand Career Option: With increasing cyber threats, organizations are actively hiring cybersecurity professionals.
- Be Future-Ready: Equip yourself with a skill set that is critical in today’s digital-first world.
Showcase Your Achievements
Offsec's Industry-Leading Professional Certifications
Learn Tools Used by Professionals
Tools Covered






























What others have Asked
FAQs
1. What are the prerequisites for Ties Certified Security Associate Course?
There are no formal prerequisites for Ties Certified Security Associate Course. However, basic computer literacy, familiarity with operating systems, and a willingness to learn are recommended.
2. Who is the Ties Certified Security Associate Course suitable for?
This course is ideal for beginners, students, IT professionals, and anyone interested in cybersecurity. No prior knowledge in cybersecurity is required, making it perfect for those starting their journey in the field.
3. Is there a prerequisite for enrolling in this course?
4. What kind of certification will I receive upon completion?
5. Are these courses available offline & online?
6. What competencies will I gain?
Upon completing Ties Certified Security Associate Course, you’ll gain a fundamentals in:
– Cybersecurity fundamentals and frameworks
– Basics of Network Security
– Fundamental Practical skills for entry-level cybersecurity roles
7. Is there any support available after completing the course?
Yes, Ties Infotech provides career support to help you find job opportunities.
8. How can I enroll in this course?

Ties Institute
PHONE NUMBER
+91 70582 29371
tiesinfotech@gmail.com
LOCATION
Pune, Maharashtra